Celebrating 33 years of Pretty Good Privacy
As the internet grows in complexity, so does the importance of online security. Let’s take a closer look at a key encryption program that has reshaped safe communications in the digital world.
This June marks the 33rd anniversary of Pretty Good Privacy (PGP), a powerful end-to-end encryption program that enables secure and private exchange of information on the internet.
Today, we’ll discuss how it works in simple terms, how it’s linked to cryptocurrencies, and how you use it every day without even knowing!
What is PGP?
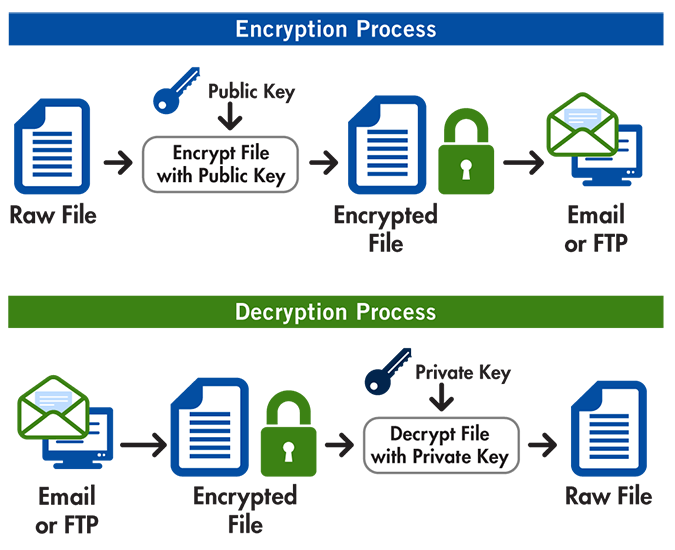
PGP is a method of encrypting and decrypting data to ensure that only the intended recipient can read it. It uses “asymmetric cryptography”, a method of encryption that uses a pair of keys to ensure privacy.
- Public and private keys: PGP uses a pair of cryptographic keys – public keys for encrypting messages and private keys for decrypting them, so that only the intended recipient can read the message.
- Zero plaintext data: Service providers, ISPs or hackers cannot read the encrypted communication. Even if intercepted, the data cannot be deciphered without the private key.
- Secure key exchange: Users exchange their public keys to allow secure communications. They keep their private key only to themselves, just like you would never share the private key to your hardware crypto wallet.
Once the two parties have exchanged their public keys, PGP ensures secure communications like this:
- Encryption: When you send a message using PGP, it’s scrambled into an unreadable format (encrypted), and can only be decoded with the recipient’s private key.
- Decryption: The recipient uses their private key to convert the encrypted message back into the original, readable format.
- Digital signature: PGP allows users to digitally sign their messages, verifying the sender’s identity and ensuring the message hasn’t been altered.
PGP is used everywhere
Many people use PGP every day without even realizing it. The principles of PGP have been integrated into popular applications and services, and you will find it wherever advanced security is needed. Some examples include:
- Mainstream chat platforms: Signal, Telegram, WhatsApp and even Messenger now all use end-to-end encryption based on asymmetric cryptography.
- ProtonMail: This encrypted email service has used PGP since its beginning.
- FileVault: Apple’s built-in disk encryption system for macOS uses PGP-based encryption to protect user data.
- Plugins and extensions: PGP is widely available as an add-on for email and other forms of communications.
- Enterprise and government: Large entities leverage PGP principles to protect sensitive communications, classified documents, and critical infrastructure.
PGP and cryptocurrency
The principles behind PGP encryption are closely related to those of cryptocurrency transactions:
- Public and private keys: Both PGP and cryptocurrency use a pair of cryptographic keys. In PGP, these keys encrypt and decrypt messages. In the world of crypto, they manage wallets and secure transactions.
- Digital signatures: PGP uses digital signatures to verify messages, and cryptocurrencies use them to validate transactions. PGP uses the SHA-256 cryptographic hash function for signatures, and this is also used in Bitcoin’s proof-of-work consensus mechanism when creating unique transaction IDs.
- Decentralization: PGP lets individuals to secure their communications independently of a centralized service, much like how the blockchain allows users to manage their finances without relying on third parties. With PGP, users don’t have to trust a provider, and instead verify the data integrity themselves.
Read more about Pretty Good Privacy in the words from its creator, Phil Zimmerman: https://philzimmermann.com/EN/essays/PGP_30th/
Building on PGP’s legacy at Confirmo
As the leading crypto payment gateway, we’ve built upon PGP’s foundational principles to create a highly reliable infrastructure for cryptocurrency transactions. Our infrastructure uses advanced cryptographic techniques to make sure every processed payment is secure and verifiable, and Confirmo has never been breached or hacked since its founding in 2014. Learn more about how we help you maximize account security here.
We can help your company leverage blockchain security easily by combining these cutting-edge security features with blockchain technology. Our custodial infrastructure reinforces crypto’s inherent benefits while saving you the technical hassles of directly interfacing with blockchains. Leave that to us, and focus on your business priorities.
Whether you’re a small business owner looking to accept your first crypto payment or a large enterprise aiming to optimize existing payment flows, Confirmo is here to help you navigate the world of digital finance. Start accepting crypto payments today!


